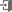When you need MONITORAPP
Applications and data within them are the biggest assets of your business.
Attackers know its value better than anyone else, so they don’t stop attacking applications.
Applications are easy to attack because they are located at the top of the OSI layer.
The fact that applications run not just the code, but everything
around them—architecture, configuration, and other assets— adds to
the importance of application security.
U.S. Breaches in 2018 by Cause (%)Security breaches and types of attacks that exploit application vulnerabilities vary and are evolving every day.
To respond to these attacks, you need an ‘Application Firewall’ solution to block attacks on applications, an ‘APT Prevention’ solution to prevent continuous and intelligent theft of information to specific targets, and a ‘DLP’ solution to prevent leakage of information from inside.
– Application security vulnerabilities are also emerging as application usage for the enterprise business continues to soar. An application Firewall specifics to the protected servers play a key role to prevent a variety of application security threats, and the security area of the applications is expanding.
– An application firewall is a type of firewall that controls the traffic of an application or service. Application Firewall uses a set of configured policies to determine whether to block or allow communication with apps. Traditional firewalls control the flow of data with the CPU to check each packet as it passes. Application firewalls are moving further by controlling the execution of files or code by a particular application. In this way, even if an intruder enters a network or server, it cannot execute malicious code.
– MONITORAPP provides dedicated firewalls specialized in Web and Database for business-critical application protection. Application firewalls eliminate the security threats that are vulnerable to each application and provide continuity of service.
– Advanced Persistent Threat (APT) is a security threat to specific targets in an intelligent, continuous manner, with advanced, targeted attacks aimed at stealing confidential information. It attempts to attack by finding weaknesses, such as distributing malicious code attachment URLs to users through the Internet or e-mail, or detecting patterns of PC users Victims are unaware of the extent of the damage as well as the fact that they have been victimized.
– ‘APT’ takes information in four stages: penetration, trenching, collection and leakage. Attackers infiltrate the network, gather internal information over a long period of time, plan the next step, and proceed through the discovery phase. Once the relevant data has been collected, intelligent continuous threats are concluded by either leaking information or damaging the system during the leakage phase.
– The ‘Operation Aurora’ incident, which took place in August 2011, has been reported to have cost more than 70 locations, including Google, U.S. government agencies, and government agencies and businesses in each country, over five years. In July of the same year in Korea, ‘SK Communications’ was attacked by ‘APT’, and the personal information of about 35 million people was leaked.
– MONITORAPP’s AISWG (APPLICATION INSIGHT SECURE WEB GATEWAY) is a secure web gateway solution that protects enterprise internal web users from a variety of evolving web attack threats, such as APT attacks, and ensures a safe web use environment for internal users within the enterprise user .
– DLP stands for Data Loss Prevention. Internal information leaks can cause huge losses to companies’ critical information assets and cause financial damage. It’s not just the IT department that takes a hit from the attack but it damages the company as a whole due to a huge loss of credibility which is the biggest asset to the business.
– Internal information is not only generated by external hacking, but also by intentional or accidental leaks from insiders. 50% of data leakage is ‘malicious cyber-attack’ such as hacking or DDoS, but 27% of data leakage due to ‘internal system fault’ and 23% of data is counted internally as ‘executive error'(2019,IBM). The introduction of DLP solutions is necessary to respond to the growing threats of valuable information.
– MONITORAPPs protect corporate information from the inside as well as the outside with network DLP solutions.