SWG Virtual Edition
AISWG-VE
SWG is essential to protecting internal users in the enterprise.
With cloud environment resources, you can operate more efficiently.
AISWG-VE is a virtual secure web gateway designed for cloud environments.
Enjoy the convenience of the cloud environment with AISWG-VE.
AISWG-VE perfectly recreates all of the appliance-based features on the cloud.
AISWG-VE perfectly recreates all of the appliance-based features on the cloud.
AISWG-VE (APPLICATION INSIGHT Secure Web Gateway-Virtual Edition) in MONITORAPP is a virtualization version of AISWG, a secure web gateway in the form of software designed to be optimized for cloud environments.
Virtualization software the features and benefits of AISWG are replicated.
AISWG-VE is a secure web gateway running in a cloud environment. The greatest advantage is that the software type provides the same superb security features as the appliance type. It is composed of PAC-based forward proxy mode suitable for the virtualization environment and can be easily used by importing image files to the cloud platform.
Secure Web gateway optimized for the cloud.
AISWG-VE supports a variety of virtualization environments (hypervisors), including KVM, Xen, VMware, ESX (i), MS Hyper-V, and IBM Z / VM so it runs perfectly on various IaaS platforms, including GCP, Gabia’s Gabia Cloud, and Alibaba’s Alibaba Cloud.
Block all paths to a malicious website.
AISWG-VE protects against malicious codes by blocking access to harmful and non-work-related sites through URL category filtering based on more than 140 million URL DBs.Thus blocking malicious URL access and attachments including malicious URLs. It protects personal information and corporate assets by blocking command-and-control communication by zombie PCs as well. AISWG works with AILabs, a threat intelligence platform that Monitorapp’s own, to increase the accuracy of URL filtering in real-time. AILabs runs MUD (malicious URL detection) system that can visit web sites dynamically with high speed. AILabs collects, analyzes, updates, and automatically categorizes the malicious URLs from the sites it visits to reflect them in the AISWG. It can also proactively respond to known vulnerabilities by providing information about Drive-by Download vulnerabilities and others.


Prevent business losses.
AISWG increases business efficiency by monitoring internal client web access. Block access to non-working sites to reduce business loss. In particular, approximately 750 applications are controlled in 22 groups, including file transfer, remote access, VPN, Game, SNS, Mail, and Messenger. AISWG also has a function to prevent leakage of important internal information. It provides network-based DLP functionality to prevent leakage of personal information or internal documents of PC users.
Ensure performance and availability.
Even in the cloud environment, our TCP stack is used to ensure high performance and reliable traffic handling.
It provides PAC-based redundancy (HA) configuration, and you can install the agent on the client to force the PAC setting (optional), and perform a health check for AISWG-VE to automatically disable PAC when a system error occurs.

SSL traffic controls enhance security
It provides all security functions including encryption and decryption for SSL traffic (HTTPS) on its own without a separate system and provides increased convenience for automatic certificate distribution for SSL encryption and decryption. Also, it improves security by providing a detection function for an invalid SSL certificate which is mainly used by C & C server or exploited web server.
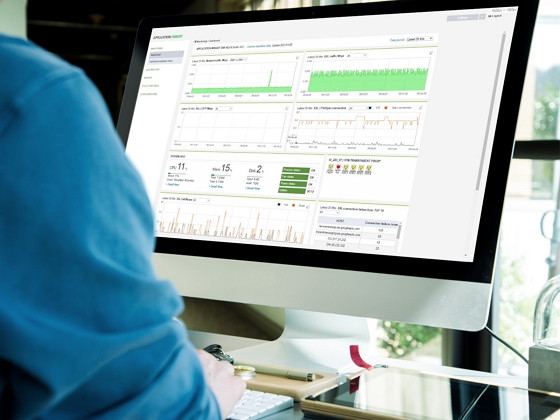
Intuitive UI and various management features
Intuitive UI makes it easy to see the status quo.It helps you to set policies flexibly and more easily by Individual control rights to non-business sites, user-specific policy settings, exception URL settings and so on. You can also monitor real-time network traffic and system status as.
AISWG Brochure
Category filtering
+ Pattern-based detection of malicious code infiltrations in web response
– 9 categories
– AI Cloud Center
– Malicious software
– Botnet
– Spam
– Abused site
– Phishing / Fraud
– Unanimous service
– Network error
– Unused domain
– AI Cloud Center
– Malicious software
– Botnet
– Spam
– Abused site
– Phishing / Fraud
– Unanimous service
– Network error
– Unused domain
+ Allow / block for general category
– 57 Category
Malicious site filtering
+ Blocking access to harmful sites according to the ration category of the Korea Communications Commission
– Malicious site detection
– Malicious site rating
– Regular expression detection
– IP detection
– URL detection
– String detection
– Malicious site rating
– Regular expression detection
– IP detection
– URL detection
– String detection
Apply malicious site-specific policy
User defined keyword input function
Regular expression pattern input and check function
WEB filtering
+ Data leak prevention and payload control through keyword / content size checking for request / response
– Total content size
– Individual parameter size
– Personal information detection
– File upload / download detection
– Keyword search
– Search for regular expressions
– Individual parameter size
– Personal information detection
– File upload / download detection
– Keyword search
– Search for regular expressions
User defined keyword input function
Regular expression pattern input and check function
Malicious code detection
+ Pattern-based detection of malicious code infiltrations in web response
– Redirect
– Command code
– Exploit Kit page
– JS obfuscation etc.
– Command code
– Exploit Kit page
– JS obfuscation etc.
Bypass connection and application control
+ Non-standard web traffic control
– Traffic violating of RFC protocol detection
+ Non HTTP control
– Block or bypass non web traffic when service port use web service port such as HTTP(80), HTTPS(443)
+ Proxy and bypass connection blocking
– Service port control (TCP / UDP)
– Anonymous(Tor, VPN Services) IP detection
– Anonymous(Tor, VPN Services) IP detection
+ Application control
– NetApps control except for web traffic such as P2P, IM, webhard, cloud-service
Easy User setting
Flexible policy formulation
+ User based policy setting
– Apply policies for each user or group
– Easy security policy establishment
– User specific statistical information / logs
– Easy security policy establishment
– User specific statistical information / logs